Table of Contents
This section provides examples of how to decrypt encrypted backups with Backup Ninja.
Decrypting a backup with Backup Ninja agent
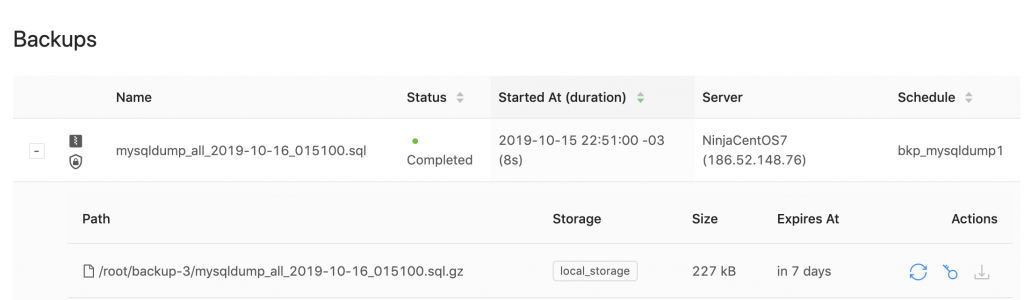
Firstly, go to Backups → choose the backup that you want to decrypt → Actions → click on the “key” icon, as shown in the following screenshot:
You will get a pop-up where it shows the commands to decrypt the backup:
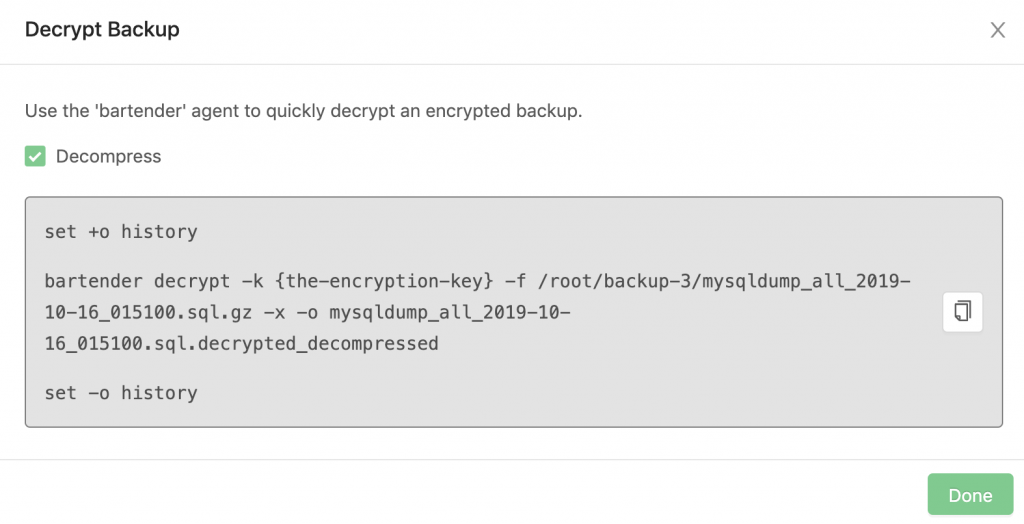
Then, on the database node, run the provided commands:
$ bartender decrypt -k {encryption-key} -f /path/to/backup.tar.gz -x -o backup_decrypted.tar
$ tar xvf backup_decrypted.tarIf compression is not enabled, remove the -x flag from the command above. Example:
$ set +o history
$ bartender decrypt -k 14ca46fc2d501eac6381034e8158c19dxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx -f /backups/backup-3/pg_basebackup_all_2019-10-14_214500.tar.gz -o pg_basebackup_all_2019-10-14_214500_decrypted.tar
$ tar xvf pg_basebackup_all_2019-10-14_214500_decrypted.tar
$ set -o historyWe strongly advise running the decryption commands between set +o history and set -o history to avoid storing the key in the user’s history.
Decrypting a backup manually
You can also decrypt the backup manually by using OpenSSL.
$ echo '{encryption-key}' | xxd -r -p > /tmp/aes.key
$ cat /path/to/backup.gz | openssl enc -d -aes-256-ofb -pass file:/tmp/aes.key > backup_decrypted.gz
$ gunzip backup_decrypted.gzIgnore the last step if compression is not enabled. Example:
$ set +o history
$ echo '14ca46fc2d501eac6381034e8158c19dxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx' | xxd -r -p > /tmp/aes.key
$ cat mysqldump_all_2019-10-18_230300.sql.gz | openssl enc -d -aes-256-ofb -pass file:/tmp/aes.key > mysqldump_all_2019-10-18_230300_decrypt.sql.gz
$ gunzip mysqldump_all_2019-10-18_230300_decrypt.sql.gz
$ set -o historyWe strongly advise running the decryption commands between set +o history and set -o history to avoid storing the key in the user’s history.